2010 January
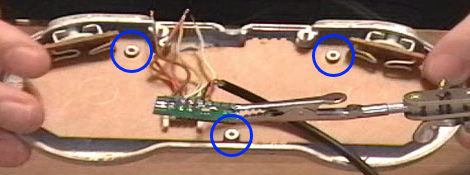
Super Nintendo - USB Controller
Wouldn’t it be great to be able to play video games on your PC with a Super Nintendo Controller!? Well, now you can! SNES USB Controllers can be quite expensive if you buy them already pre-made, but if you purchase a kit and an old used SNES controller, you can save a bundle.

E-mail - Introduction
There isn’t a moment that E-mail isn’t being used by someone somewhere in the world. In today’s world it is very common for most teens and adults to use E-mail at least once a day, but often even way more than that. Even though E-mail is so widely used, it’s not common knowledge as to how E-mail works beneath the hood. Here is my attempt at a brief overview of E-mail.

E-mail - Send Fake Email’s
Make sure you’ve already gone over the E-mail – Introduction tutorial which covers how E-mail works beneath the hood. It’ll provide a good overview into what we’re about to go over.

Google Hacking - Protect Yourself
The second part of this series will cover how to use those advanced search operators to find a variety of security flaws out there on the web, proving how Google doesn’t only index the good, it can index the bad. Rest assured, you will also be shown ways that you can make sure Google isn’t indexing your sites security flaws or even just things you may not want out there for everyone to find.
Google Hacking - Introduction
Even though Google is as big and powerful as it is, people don’t seem to realize the full potential Google has in the area of Hacking/Security. For that reason, I’m here to explain to you why Google should be one of your major tools in Ethical Hacking and protecting yourself!
