2012 April

Lock Picking - Tumble Locks

Wifi Network - Change MAC Address

Wifi Network - WEP Cracking

Extract / Mount - Mounting
There are plenty of instances where games, movies, or whatever are transformed into images. These images are optimal because they can be instantly burned, mounted, or played (video). The most common formats you’ll run across are ISO and BIN.

Extract / Mount - Extract & Repair
There are many types of files you may come across when browsing the interwebs so you’ll need an arsenal of tools to handle them. Here is a short list of extraction types you’ll want to be able to handle:
- RAR Files
- 7z Files
- ZIP Files
E-mail - Protect Yourself
Email security can be a real concern for a lot of people. One of the biggest issues is making sure that the only person able to read the e-mail you sent, is the person you intended to read it. Another issue is making sure that an email you received is valid, and not an impersonator.
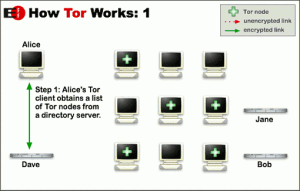
Browse - Anonymity
Privacy is a big concern for a lot of people when it comes to online activities. There are a lot of good (and bad) reasons to want to remain anonymous. But most people just don’t know how, because it’s too far over their head. However, as I’ll be showing, Tor makes it easy for anyone to stay anonymous whenever they want.
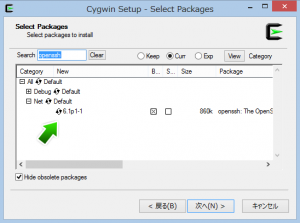
Browse - Security
By setting up an SSH server that can be reached from the web (either a hosting service you pay for or you configure your router to open the port you choose to use for SSH), you can create a tunnel from wherever you are, to your SSH machine, which then goes out to the internet. By doing so, you can both secure your connection as well as bypass any work/hotel/etc proxy servers.

Browse - Introduction
There are three main areas and/or topics that seem to come up surrounding online browsing. Those are: security, anonymity, and getting past/around proxy servers. We cover the in depth stuff on other pages, but read this first to get a simple introduction to what each is.
Continue reading…
