2012 May

Password Cracking - Linux
Once you’ve got a hold of a Linux password hash, you’ll need something to crack it, and we’ve got just the thing. John the Ripper is a cracker available for both Windows and Linux, and can utilize both brute force and wordlist cracking methods.

Password Cracking - Windows
Windows passwords are either LM or NTLM hashes. While you can’t get direct access to the password, you can’t get direct to the password hash and then attempt to crack it. There are quite a few ways, along with quite a few tools to accomplish this task. We’re going to show you just how easy it can be to crack a Windows password if it isn’t secure (complicated) enough.

Stealth - Hide / Restore Hotkey
Ever been somewhere where you wanted privacy, because you want to browse the internet freely or play a video but don’t want to get caught? (Like at work? 😉 ) Let us show you how to create the ultimate hotkey macro to allow you to hide all those applications via the click of just one button!

Portable - GBA / NDS / 3DS
If you’ve ever wanted to be able to load roms onto your Nintendo Gameboy (GBA, DS, 3DS, etc), then look no further. We’re about to show you just how easy and simple it can be. All you’ll need is a simple tool can a flash cart/card which can be purchased quite cheaply!

Stenography - Hide in Images
Ever want to know how pass around secret messages? In this tutorial, you’ll learn how to hide encrypted text inside of images so that not only would the recipient have to know it’s inside the image, but also know the password to be able to make any use of it.

Stenography - Hide in Text
If you’ve ever wanted to learn how to hide a secret message inside another message, you’ve come to the right place! Hiding secret messages is every kids fantasy and it’s pretty awesome to learn how to do it even if you’re no longer a kid. Aren’t we all still kids on the inside anyway?

Browse - Bypass Proxies
So maybe your work or dormitory has an internet proxy that blocks you from being able to browse to certain websites or play video games. When there is a will, there is a way. We’re going to show you how you can get past those pesky proxy servers once and for all!
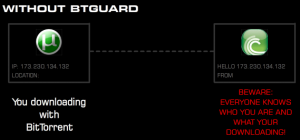
Peer-to-Peer - Protect Yourself
If you’re torrenting without going through any sort of proxy, then that means your IP address is directly visible to anyone when you connect them to download or seed a torrent. It basically means you have no security or anonymity whatsoever. To remedy this, it’s best to torrent through a VPN proxy service.
