Web / Network

Browse - Bypass Proxies
So maybe your work or dormitory has an internet proxy that blocks you from being able to browse to certain websites or play video games. When there is a will, there is a way. We’re going to show you how you can get past those pesky proxy servers once and for all!

Wifi Network - Change MAC Address

Wifi Network - WEP Cracking
E-mail - Protect Yourself
Email security can be a real concern for a lot of people. One of the biggest issues is making sure that the only person able to read the e-mail you sent, is the person you intended to read it. Another issue is making sure that an email you received is valid, and not an impersonator.
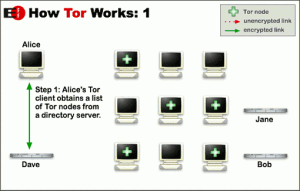
Browse - Anonymity
Privacy is a big concern for a lot of people when it comes to online activities. There are a lot of good (and bad) reasons to want to remain anonymous. But most people just don’t know how, because it’s too far over their head. However, as I’ll be showing, Tor makes it easy for anyone to stay anonymous whenever they want.
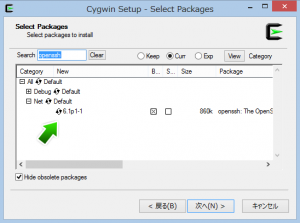
Browse - Security
By setting up an SSH server that can be reached from the web (either a hosting service you pay for or you configure your router to open the port you choose to use for SSH), you can create a tunnel from wherever you are, to your SSH machine, which then goes out to the internet. By doing so, you can both secure your connection as well as bypass any work/hotel/etc proxy servers.

Browse - Introduction
There are three main areas and/or topics that seem to come up surrounding online browsing. Those are: security, anonymity, and getting past/around proxy servers. We cover the in depth stuff on other pages, but read this first to get a simple introduction to what each is.
Continue reading…

Database - Introduction
Databases may vary in how they work beneath the hood, how you interact with them, etc but after all is said and done, their purposes are always the same: store data for retrieval. Without databases, managing content such as user accounts, would be very tedious and sloppy.
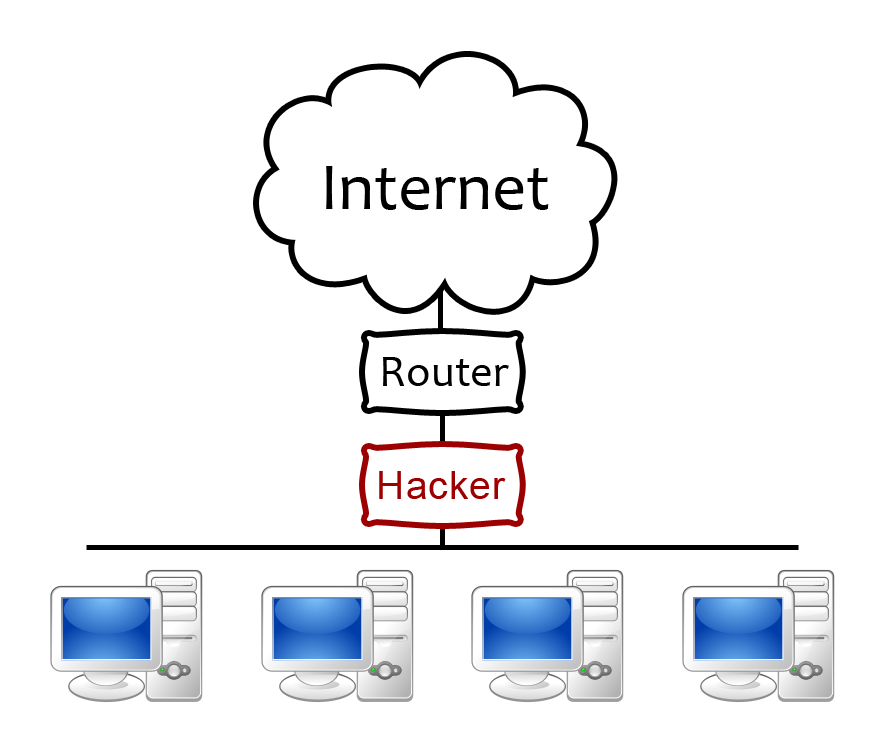
Local Network - Man-in-the-Middle Attack
A man-in-the-middle attack is one that is most commonly performed on a local network, because that is the easiest way to exploit its benefits. Essentially, a man-in-the-middle attack is exactly what it sounds like. You become the man in the middle, between your victim and their target destination. Let’s go over this with an example.
Local Network - Introduction
Nothing can exist without having a local network. At home, work, or any where you go there is a local network if a PC is connected to the internet. There may only be one user connected, but the possibility of more is always looming. Local networks attacks are a tremendously big deal. It’s the difference between an attacker being on the outside of your house and trying to attack you versus already being inside your house. Which poses a bigger threat? Exactly..

