E-mail - Send Fake Email’s
Make sure you’ve already gone over the E-mail – Introduction tutorial which covers how E-mail works beneath the hood. It’ll provide a good overview into what we’re about to go over.
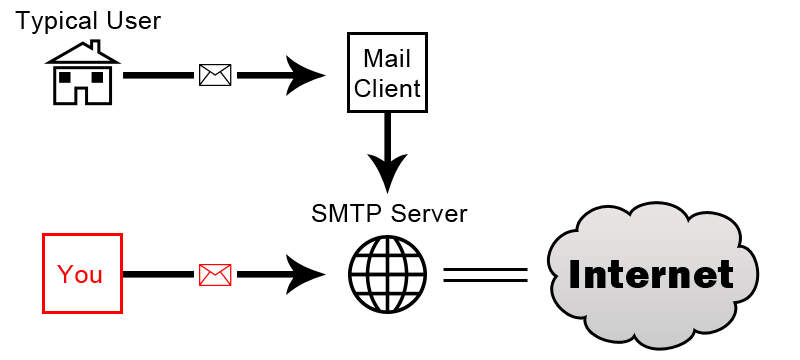
You’ve already seen how SMTP generally works in real life situations, but you haven’t seen how we plan on using it. The idea is very simple, we’re going to take out the Mail Client and connect directly to the server our self. The diagram below presents a good visual example of what we are going to be doing:
The next step is choosing which method is right for you: Hand Forging Fake E-mail’s, Fake E-mail Services, or my personal favorite.. Fake E-mail Web Script.
Hand Forging Fake E-mail’s
Ways to Find a Server
There are a few different ways you can find a server that you can use.
- Anonymous Identification (relaying)
- User Account Identification
- IP Address Identification
Anonymous identification simply allows you to connect to a server without requiring an account or identification. These types of servers are becoming quite hard to find, for obvious reasons. Using an anonymous identification server to send E-mail is known as relaying.
User Account Identification is the act of using a server that you have an account with to leverage those permissions so that you can send a fake E-mail. Usually all this requires is providing false information when setting up your Mail Client, etc. This is will result in the E-mail looking fake to the untrained eye, but someone who knows how these things work will be able to easily look at the E-mail header information.
IP Address Indentification is when you’re sending out mail using your own network’s SMTP server to send the forged E-mails. For instance, often ISP’s will dedicate your IP to being able to send out E-mail through their SMTP server because you’re basically in their network. Another example would be to send out an E-mail from a work or school(college campus) environment, which generally have their own SMTP servers as well.
Actually Finding a Server
Servers can actually quite a pain to find because most don’t support open relaying, and even if you find one that does you also might be affected by a bigger issue. A lot of ISP’s now block connecting to port 25 on outside servers, which is what we’ll be needing to do. However, if your ISP doesn’t block that, then you’re good to go to any outside server. Otherwise, your only hope is connecting to your ISP’s mail server to be able to Hand Forge E-mail’s.
If you do happen to be able to connect to outside SMTP servers, AKA not blocked by your ISP, then here are a few utilties you can use to find out what the SMTP servers of a web address are. For example, yahoo.com, hotmail.com, etc.
Execution
I’m going to assume you already have an SMTP mail server that you found that you can connect to. So from now on, I’ll refer to that server as mx.someserver.com The first thing we need to do is to connect to that server, which you should have done once before but we need to do it again, so here it is, the command:
telnet mx.someserver.com 25
Now, if you get connected then you’re going to want to follow the steps below, otherwise you should figure out if the server is denying you or if your ISP is blocking you from connecting to port 25. Anyways, here we go:
#Anything in bold is what is already on the screen, not what you are going to type out.
#Every server varies, so the output may look a *bit* different, but that’s alright.
220 Welcome to Some Server
helo example.com <– This is what you’re going to type in to tell it who you are.
250 Hello example.com
MAIL FROM: <madeupname@example.com> <– Tell it who you want it to look like the E-mail came from.
250 madeupname@example.com Address Okay
RCPT TO: <victim@yahoo.com> <– Tell it who you want the E-mail to go to.
250 victim@yahoo.com Address Okay
data <– Tell it you want to begin forging the E-mail.
354 Ready for data; end with <CRLF>.<CRLF>
From: madeupname@example.com <– Same thing as MAIL FROM:
To: victim@yahoo.com <– Same thing as RCPT TO:
Subject: Testing Fake E-mail <– Tell it your Subject.
#Press Enter twice
This is the message body of my fake E-mail. Hellooooo! <– Type whatever you want, then hit Enter.
. <– DO NOT FORGOT TO FINISH WITH A PERIOD
#Press Enter again, it’s important
250 Mail queued for delivery.
And you’re done, that’s all there is to it! Not really that hard once you’ve found a server to connect to.
Example
For the example, I’ve just set up my own SMTP server on my own Windows box. I used Windows because most of you who use Linux and come to this website know how to get to the terminal to execute these commands. It’s the same commands for Windows or Linux. Anyway, the SMTP server is QK SMTP server. The responses you’ll receive out in the wild will be similar to this(though not identical). Replace 127.0.0.1 of my example with whatever your SMTP server name is.
Fake E-mail Services
There are few services out there that automate this process for you. I’m not going to go into how to use them as they are pretty self explanatory, especially if you’ve gone through the rest of these articles, so I’m simply going to list them off.
Fake E-mail Web Script
This method requires that you have a host somewhere that you can upload website code such as PHP, Perl, Python, etc and be able to reference the mail command. Generally, if you can run web code(PHP/Perl/Python, etc) then you have access to calling the mail command.
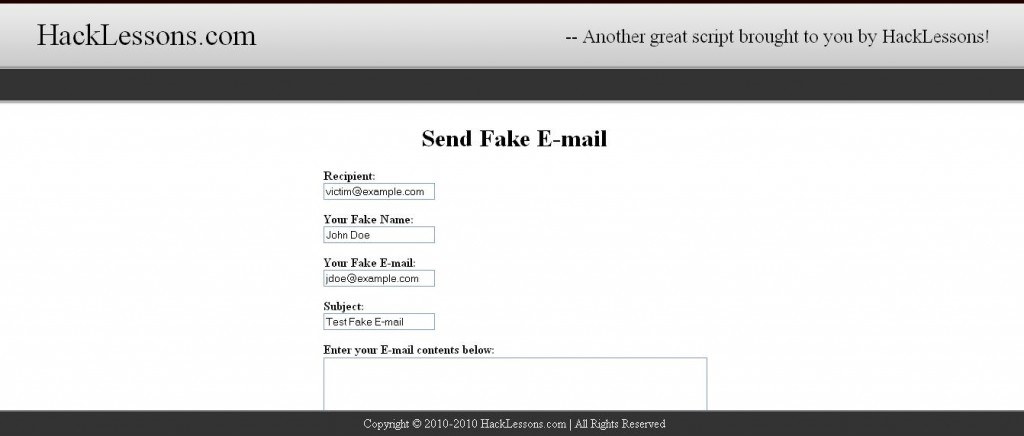
Most of you out there that are programmers already probably know where I am going with this and can write your own script to produce this result of being able to send fake E-mail’s. However, HackLessons has generated a set of scripts to help those of you out that have no clue where to begin. Simply download the scripts, upload them to your web server, and then browse to the folder path of where ever you stored the files. You’ll get an image that looks something like this:
Simply fill in the form and click Submit. I’m sure you could do much more with this form and turn it into a real masterpiece, but we’re just giving you a base to start with. Hack it to pieces till your heart is content.