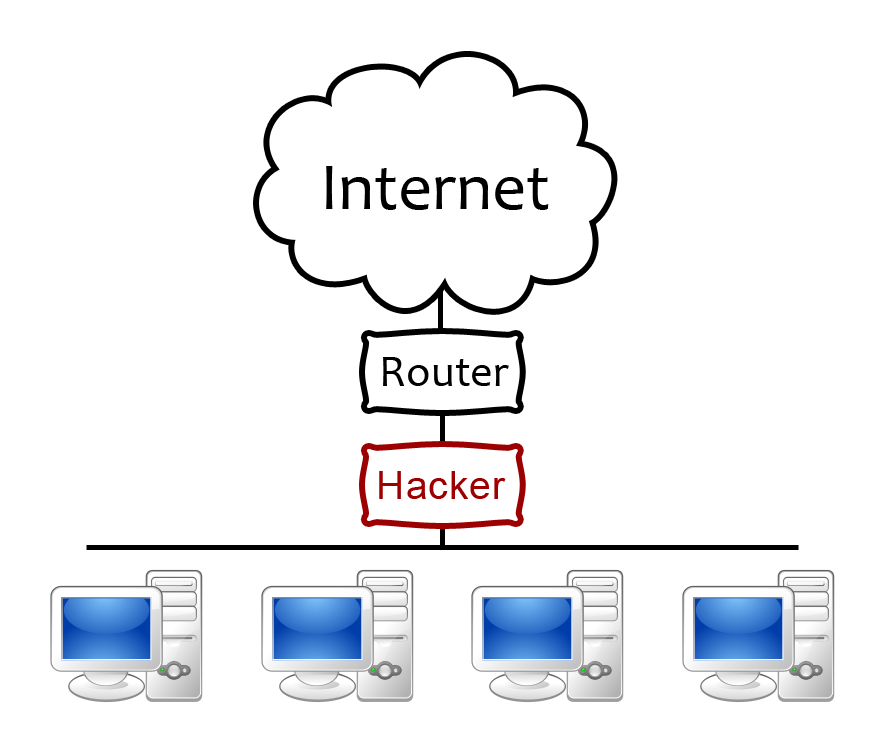
Local Network - Man-in-the-Middle Attack
A man-in-the-middle attack is one that is most commonly performed on a local network, because that is the easiest way to exploit its benefits. Essentially, a man-in-the-middle attack is exactly what it sounds like. You become the man in the middle, between your victim and their target destination. Let’s go over this with an example.
How It Works
Let’s say a user(victim) is browsing the web. The first place his data/packets go is to the router/gateway/etc that he is setup with. What you will do is pretend to be that router/gateway/etc, making his computer send those packets to you instead, while simultaneously tricking the router/gateway/etc into thinking you’re the victims computer. The reason you want to appear as the victim’s computer is because you want it to appear seem-less to the victim. You don’t want him knowing something is up. By pretending to be the victim, the data will be sent from the router to you, and then from you to the victim.
Now that you’re sitting in the middle of this connection, you’re actually able to capture the data/packets flowing between the victim and whatever he is connected to through that router. For instance, he may be browsing the web, logging into websites or his email, etc and you’ll be seeing all that traffic as it happens lives.
Windows
Demonstration
cain and able vid here
Linux/Unix
Demonstration
dsniff vid here